
HAProxy on OPNsense Firewall with Let’s Encrypt
On an Alix APU, I run an OPNSense firewall with HAProxy and Let's’s Encrypt Plugin installed.
I run the Read-It-Later Service Wallabag on Openmediavault, which I want to reach encrypted from the Internet. I have described the installation and configuration of Wallabag on Openmediavault here:
Wallabag on Openmediavault
The Alix APU’s can be found here:
https://www.apu-board.de/
More information about Let’s Encrypt can be found here
https://letsencrypt.org/
We start with the configuration of Let’s Encrypt. First we put on Staging Environment, until we are sure, that our configuration is running. We still leave the plugin itself deactivated.
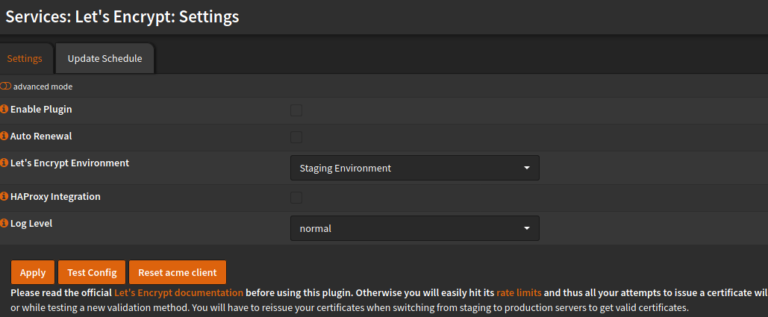
Next we set up an account. Assign your hostname, than the url, to be operated with the certificate. An email address is also stored. In the end, the account should look like this
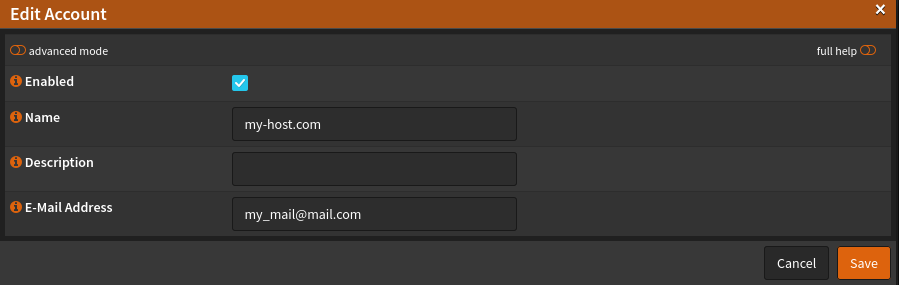
Now a method for the validation has to be chosen. We use the HTTP-01 Challenge. However, we do not do this, include the HTTP service in the HAProxa frontend to be configured later. We rely on the OPNSense web service, which automatically opens the required port. I chose this variant, the port 80 not opened with me and / or forwarded. The web service is listening on the WAN interface.
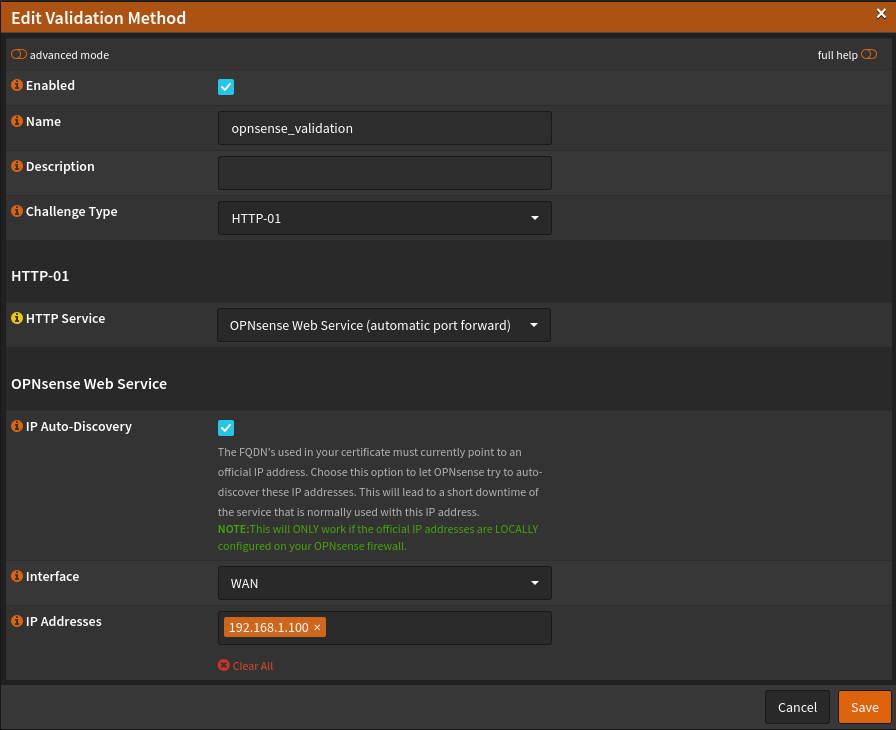
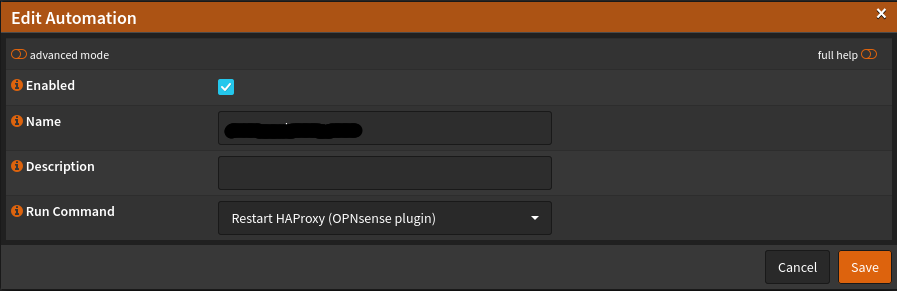
So that the HAProxy on the OPNSense firewall as HTTPS frontend with let’s encryption at the renewal also updates the new certificate externally, we set up automation, which restarts the proxy after the challenge. Simply assign a name and select the appropriate command: Restart HAProxy
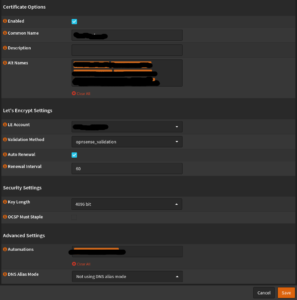
Now we set up the SSL certificate and choose that Certificates Menu aus. As Common Name we use our domain: myDomain.ltd
Under Alt Names we can assign more names, that should be covered by the certificate, such as subdomains sub.myDomain.ltd
Im Drop Down Menu LE Account we select the previously created account and do the same Validation Method. The catch with Auto Renewal is set and the interval is set to 60 set. The Key Length is 4096. Now that Automation select and Not using DNS alias mode establish.
OPNsense Let's Encrypt CertificateWe switch back to the tab Let’s Encrypt -> Settings and enable the plugin. Please check again, that Environment is on staging. For security you can also have your config tested. Now back to Let’s Encrypt -> Certificates and we force the certificate to be reissued. To do this, click on the following button
In the tab Let’s Encrypt -> Log File you can watch the process. If everything works you should see an entry at the end: “on_issue_success”
Then you can go on Production Change the environment and force the issuance of the certificate again.
Configuration of HAProxy on OPNsense
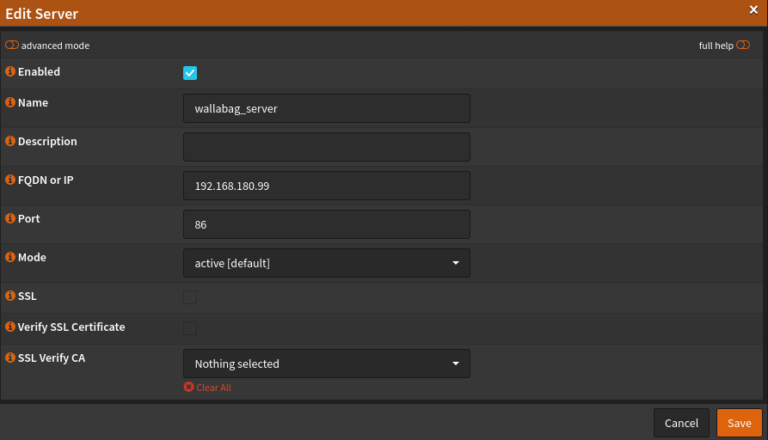
We start with the creation of a server and select the menu item Real Servers and add about that + Icon to add a new one. The parameters in the screenshots show the configuration for Wallabag, that we touched down here: Wallabag on Openmediavault
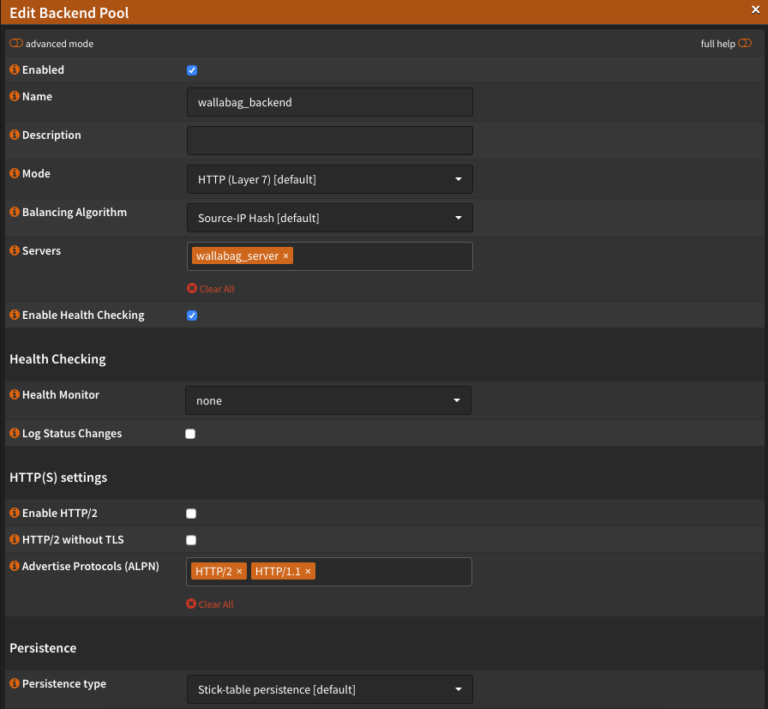
In the next step we add a backend. To do this, go to the menu itemVirtual Services -> Backend. Finally, the configuration should look like this.
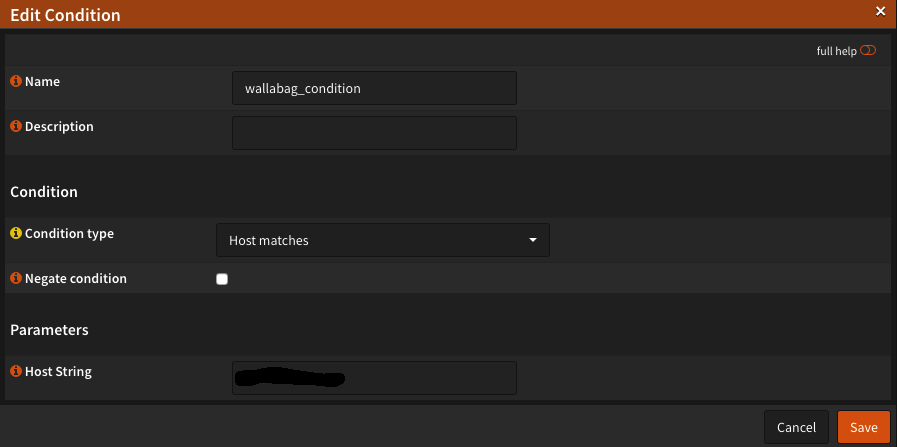
Then we move on Rules & Checks and choose Condition out. Here we set the condition, to be checked for. If you use different URLs for different pages, is the rule to chooseHost matches. The HAProxy has a variety of conditions, which can be chosen depending on the scenario. UnderHost String let’s enter our URL, under which our site can be reached. Besipiel: wallabag.example.de
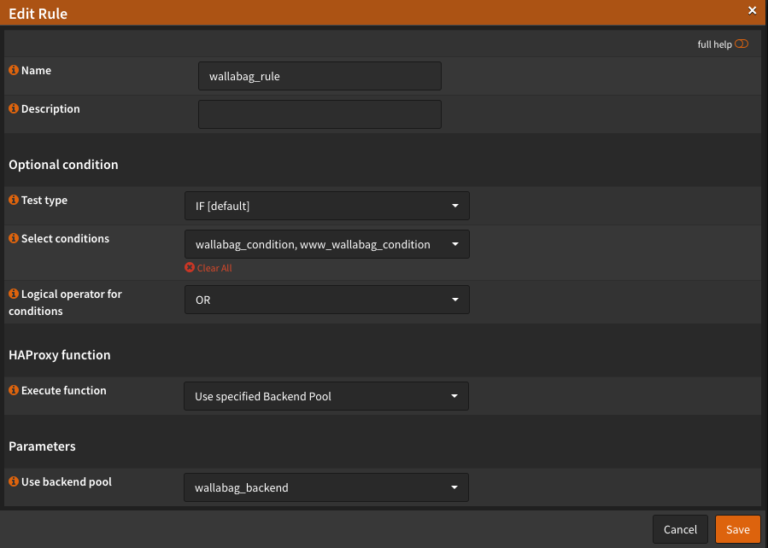
We call rules. The rule specifies, what should happen when a condition occurs. As you can see in the screenshot below, I have 2 Conditions deposited, because I want, that the HAProxy sole the connection wallabag.example.de as well at www.wallabag.example.de answers. The Test Type we leave on IF. If we have two conditions, we put that Logical Operater on OR a. After all, he should react if only one of the two is fulfilled. The function to be executed is that Use specific Backend Pool and finally we give that Use Backen Pool with the wallabag_backend an.
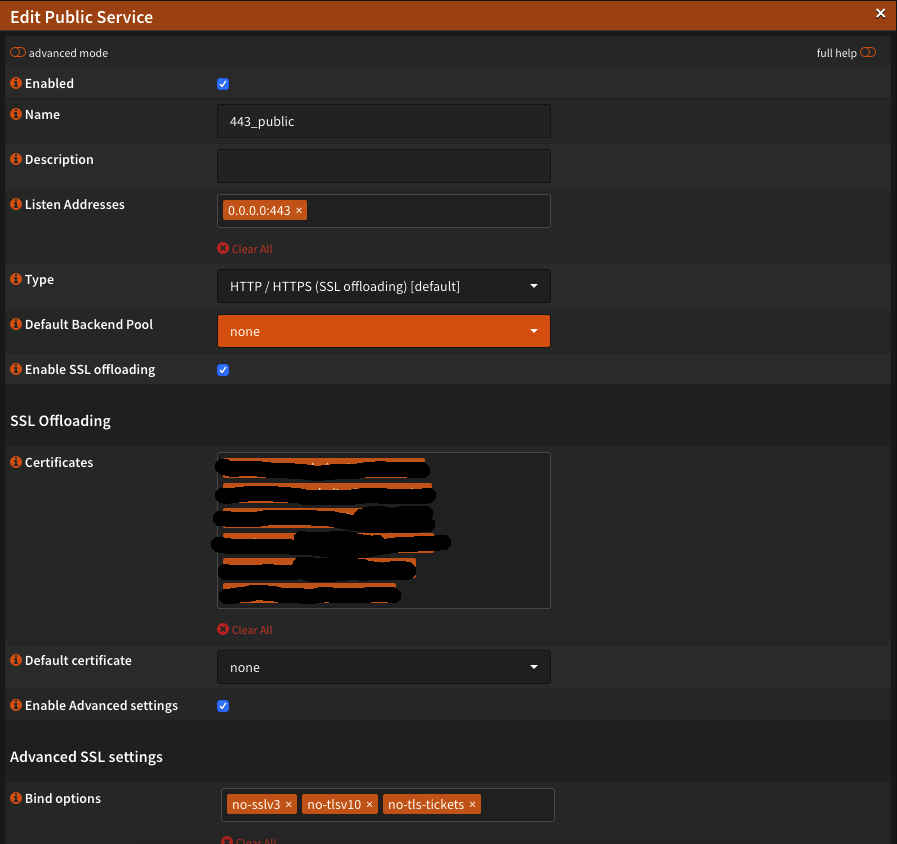
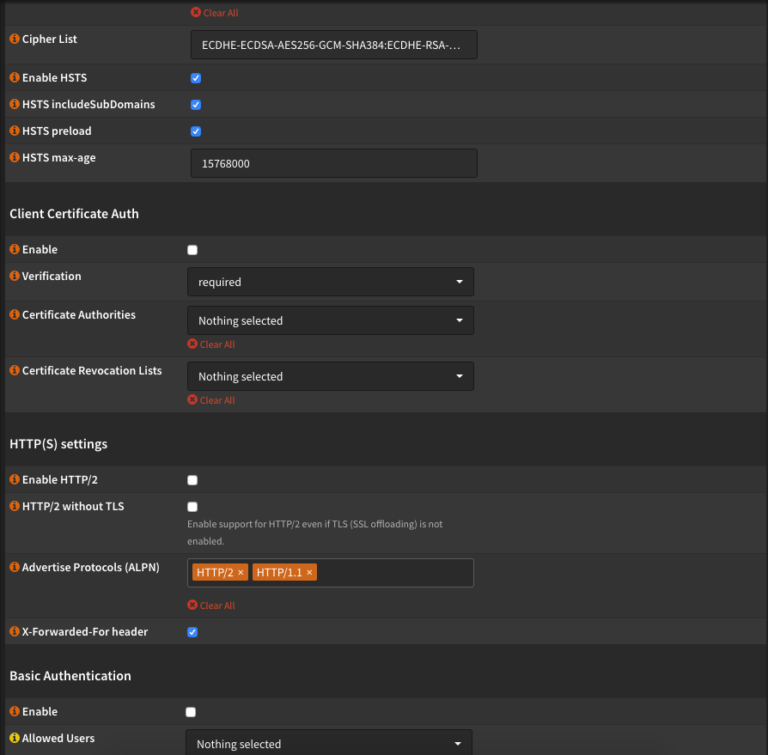
We now create one Public Frontend under Virtual Services. Most of the settings can be found in the screenshots. Please notice, that you have none Default Backend Pool have chosen. For the SSL Offloading choose your Let’s Encrypt certificate and if you only have one, you can also save it as a stationary bike. I activated the HSTS Settings. Who would like to know more about it, can read a couple of things here: HAProxy and HSTS
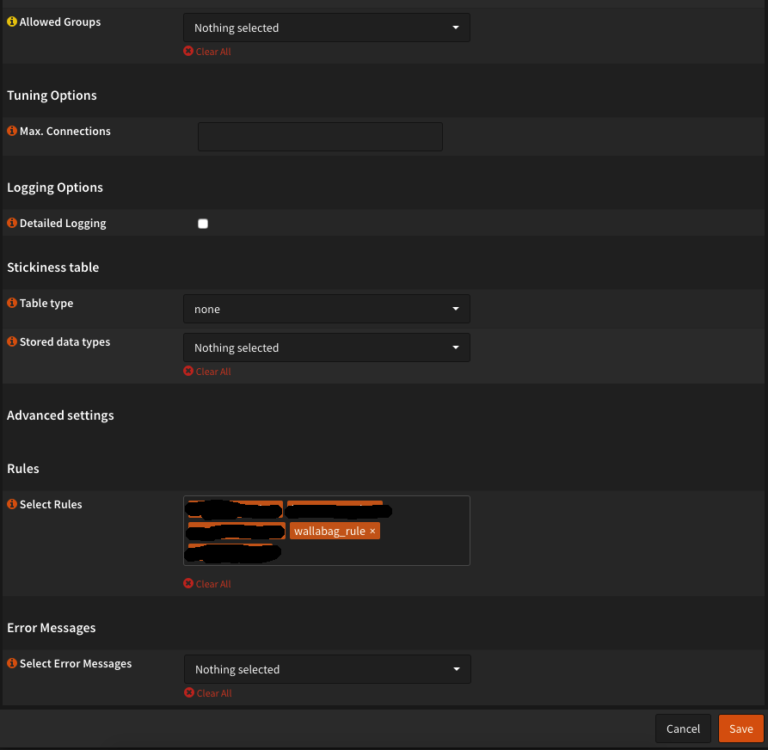
Please take care, that X-Forwarded-For Header is activated. Otherwise strange misconduct can occur. We select ours wallabag_rule and save the whole thing.
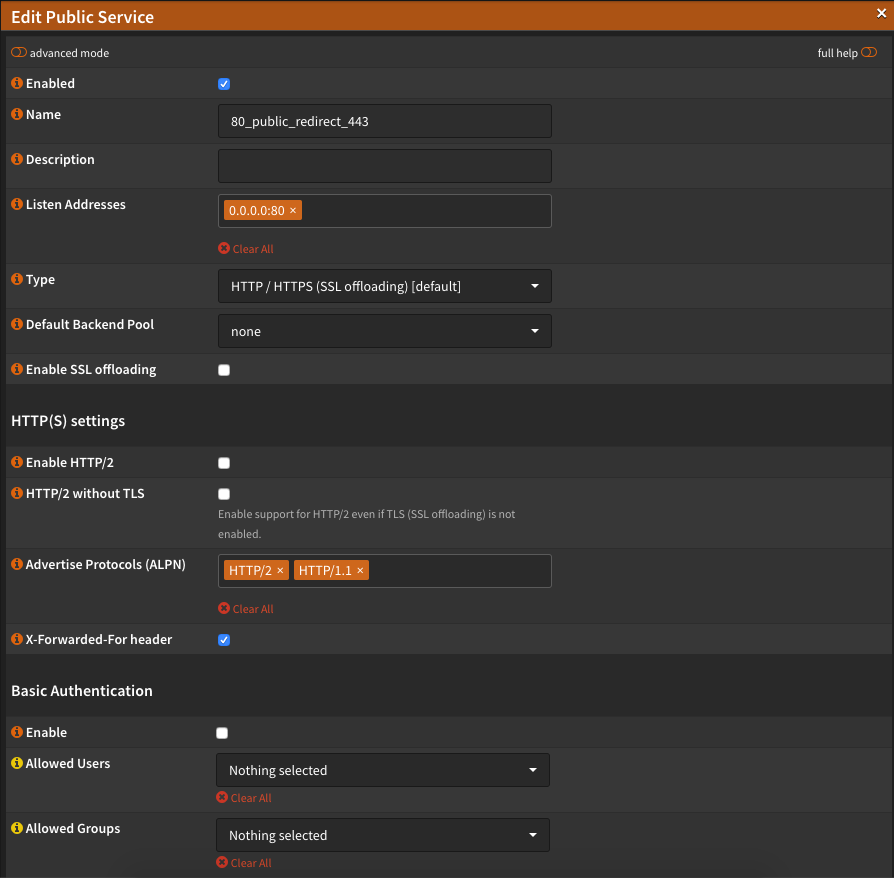
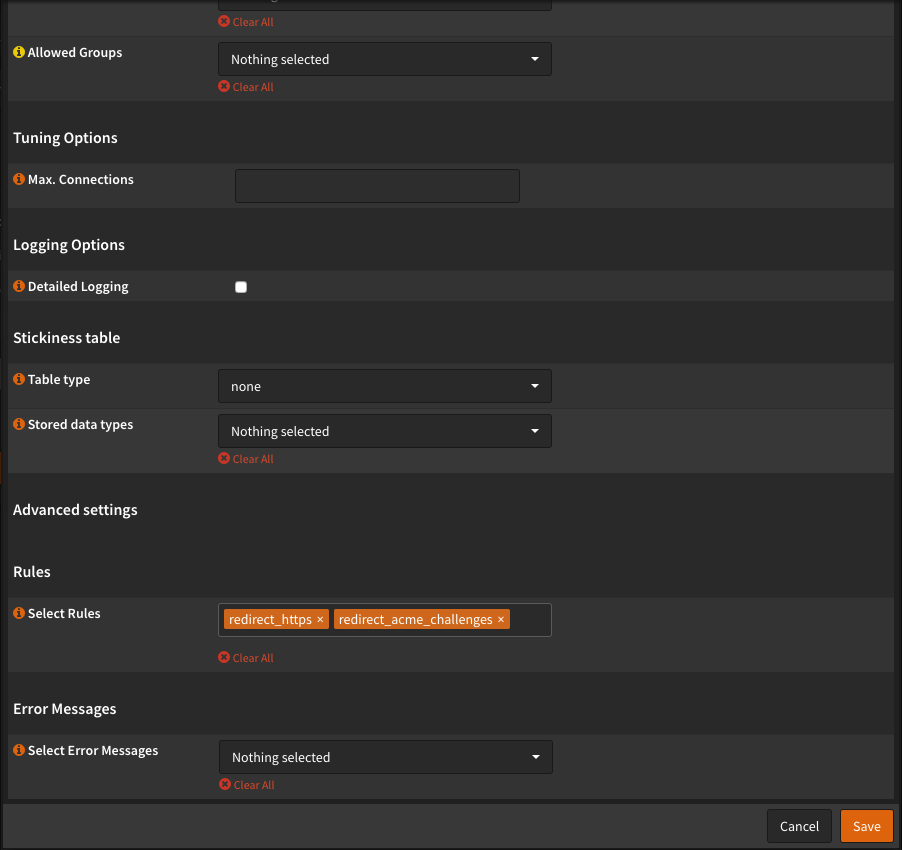
By installing the Let’s Encrypt plugin from OPNsense, most of the settings were stored in HAProxy for us and do not need to be adjusted. Just a front end for the port 80 must be created. Please make the settings as on the screenshots. The redirect-https However, you do not have a rule, therefore you only choose that Acme-return-challenge out.
Another little hint, so that everything works, you have to be among the Firewall Rules the VAN Interface port 80 and 443 on This Firewall have released. How to configure an HTTP to HTTPS redirect, I explain here …..